%20Blog%20Header%20Image%20(1).svg)
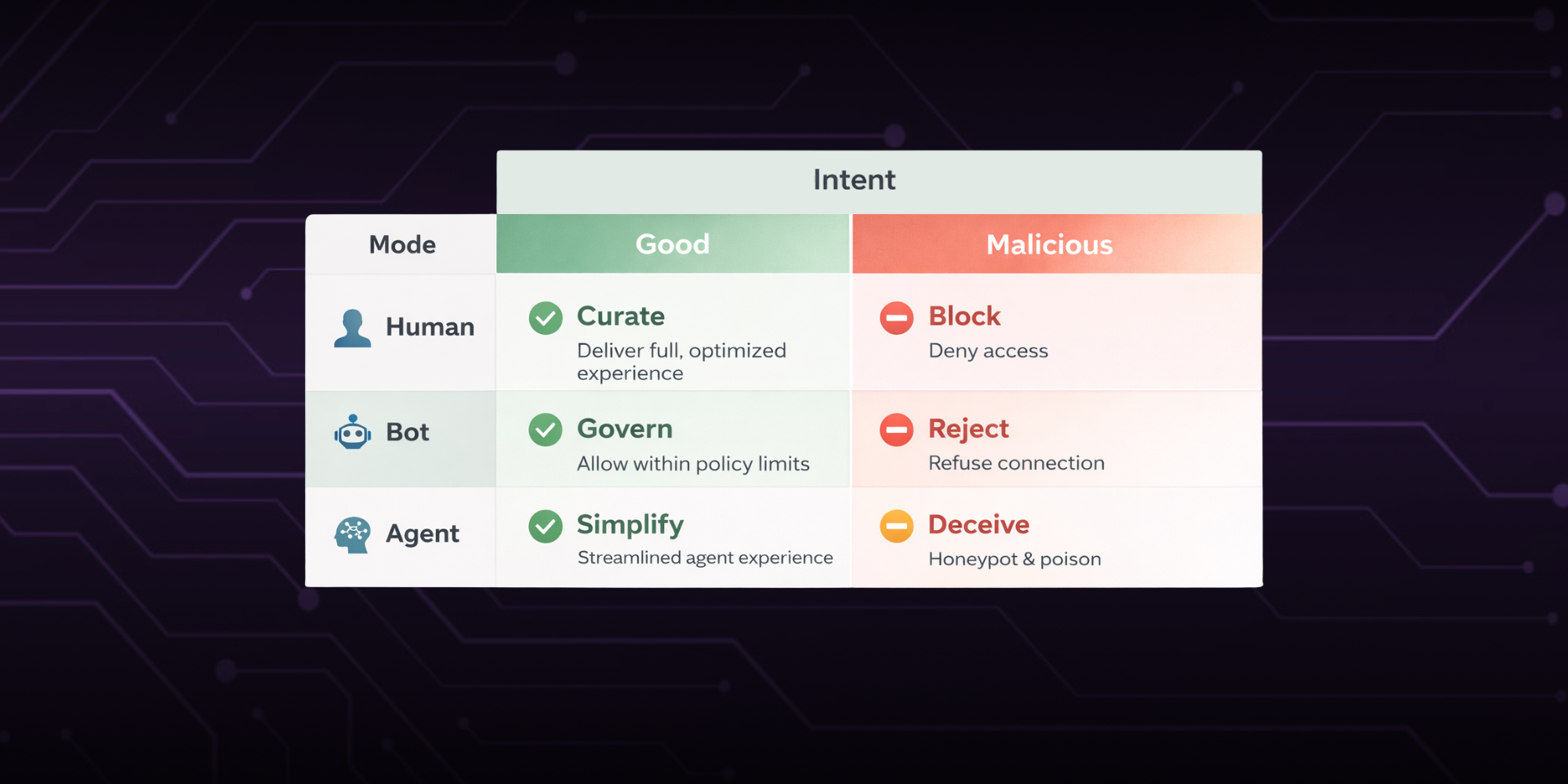
Why Bans Don't Work (and What To Do About It)
A delivery driver gets banned for misconduct. But by next week, they're back. New email. New phone. Same behavior.
This isn’t a one-off. It’s happening every day across multi-cohort marketplaces that enforce login as an operational baseline and have tried just about everything to solve this unique and complex fraud problem
Fraudsters, colluders, and repeat abusers return faster than most platforms can keep up, and they’re only getting smarter. They know how to blend in. They know how to stay just out of reach.
While most double-sided platforms rely on bans to keep bad actors out, bans only work if you can stop them from coming back.
In this post, we’ll break down why bans don’t stick. You’ll see how common signals like emails, IPs, and device IDs fall short. And you’ll learn how behavior-level detection can help you stop repeat abuse at the source, without slowing down good users.
Before the Account: A Fraudster’s Playground of Easy Entry
Most marketplaces are designed for speed and scale. Fast signups. Instant access. Low friction. That’s great for growth, but also great for fraud. When new accounts are easy to create, ban evasion becomes just another part of the playbook. Bad actors know they can slip through the cracks again and again.
Success is often measured in active users and signups. That creates a natural resistance to adding friction. After all, slowing down onboarding could mean lost revenue. But this growth-first mindset inadvertently creates a wide-open door for repeat fraud, where fraudsters can take advantage of both your features and your KPIs.
The result? A steady stream of new accounts that aren’t new at all — just recycled identities, ready to exploit your platform again.
A Common Pattern: From Fake Signups to Breaking Out
Repeat abusers don’t need a complex plan. Just a repeatable one.
They create fake accounts. Exploit promotions. Dispute charges. And when they’re done, they disappear, only to return days later with a fresh identity.
Here’s what that repeat fraud looks like in practice:
- Promo abuse: A user claims a new promo every three days by using new email and phone combinations.
- Chargeback fraud: An account skips steps in checkout, just like the last flagged fraudster.
- “Breaking out”: A delivery driver “breaks out” with an order, deletes the app, and comes back under a new name.
This isn’t just isolated behavior. It’s coordinated. We’ve seen cases where a single fraud ring uses hundreds of accounts to exploit referral bonuses, signup promotions, and lenient refund policies. Once an account is burned, they move on to the next, using the same patterns but different credentials.
And it works, because identity is easy to reset. Emails, phone numbers, and even device fingerprints can be spoofed or replaced in minutes.
ATO: When They Don’t Even Need a New Account
Not every fraudster starts from scratch. Some skip the signup entirely. Through account takeovers, bad actors hijack existing accounts with real history, solid reputations, and built-in trust. Once inside, they use that trust to operate under the radar.
This is especially dangerous in marketplaces. A fake freelancer might take over a dormant account, do a few quick jobs, deliver low-quality work, and disappear before anyone notices. The platform takes the blame. The user gets frustrated. Trust takes a hit.
And ATO rarely stops at just one account. Sophisticated attackers often manage a mix: some accounts stolen, others freshly created. The result is a patchwork of activity that looks legitimate on paper but masks a coordinated abuse ring.
Once ban evasion enters the picture, things spiral fast. A single fraudster can bounce between identities, hide behind real account histories, and escalate abuse with every login.
What makes this so hard to catch? Traditional detection tools trust the surface: a valid login, familiar device, or consistent location. But experienced fraud fighters don’t stop at the surface. They watch for what’s off:
- Sessions that move too fast
- Navigation that skips expected steps
- Timing that doesn’t match the user’s usual rhythm
These subtle shifts tell a different story — one that most platforms miss unless they’re looking at behavior.
But instead of catching that behavior, they fall back on the same move: ban the account and hope for the best.
That brings us to the next problem.
The False Comfort of a Ban
When platforms detect abuse—whether it’s a stolen account, promo fraud, or a fake signup—the response is usually the same: ban the account, block the IP, blacklist the card.
It feels like action. But for sophisticated fraudsters, it’s barely a speed bump.
That’s because signals like emails, IPs, and devices are easy to fake or reset. With a few quick changes, the same bad actor is back on the platform, ready to do it all over again.
In high-value, high-consequence marketplaces, repeat abuse is a business. Entire forums exist where users buy and sell aged, verified accounts. For food delivery, rideshare, freelance work, and wherever reputation equals revenue, there’s demand for access. A banned user doesn’t need to wait or rebuild trust. They just buy their way back in.
This cycle creates a dangerous illusion for fraud fighters: the fraud is “handled” because the account is gone. But the fraudster isn’t.
Think of a ban, then, not as the final step, but the first clue. Every ban is a behavioral signal waiting to be connected. The platforms that win don’t just block—they learn, link, and stop similar patterns before they start.
The Comeback: How They Reappear (and Why Most Tools Miss It)
Fraudsters rarely return with the same identity. But their behavior doesn’t change. They tweak just enough to get past detection. A new phone number. A slightly different device setup. A new account with recycled details from a past one. It’s the same attacker, just wearing a different mask.
This is where most fraud detection tools fall short. They focus on static signals like IP address, email, or device ID. But those are easy to fake. And session-level detection doesn’t have memory of past abuse. Every new account looks clean.
But behavior tells a different story. A bad actor might reuse patterns across multiple accounts — same usage cadence, same routes, same refund requests. But unless your system links those patterns, you’re flying blind.
This happens in marketplaces where high-performing freelancers sell their accounts, start new ones, and repeat the cycle. The original account builds trust. The copycat benefits. And the abuse continues undetected.
The challenge for platforms? Repeat fraud hides in plain sight. Each new account looks legit. But behind the scenes, it’s part of the same operation.
Why "Better Device ID" Isn’t the Answer
When fraud keeps slipping through, the instinct is to upgrade your tools. Maybe the device fingerprinting isn’t strong enough. Maybe the signals just need more precision.
But here’s the problem: fraudsters aren’t playing by the same rules. They rotate devices, spoof fingerprints, and emulate entire environments. The moment you catch up, they shift again. So you get stuck in a loop, chasing better tools that still rely on weak signals.
The real question isn’t how good your device ID is. It’s whether you're relying on device ID only. Because if a fraudster can reset their identity with a new phone or clean browser, what’s stopping them from doing it again tomorrow? Nothing.
And fraud and risk teams already know this. Device fingerprinting isn’t working anymore.
Most platforms don’t need better device ID, yet they keep shopping for them. What they actually need is a way to consistently recognize behavior. To see the same patterns across different sessions, accounts, and devices, even when every surface signal looks new.
Ban evasion isn’t a device problem. It’s a visibility problem.
A Better Way: Link Behavior, Not Just Accounts
To stop repeat offenders, you need to shift the focus from who a user says they are to how they behave. That’s the power of behavioral linking — detecting patterns that stay consistent even when everything else changes. It’s not about tracking credentials. It’s about tracking intent.
Let’s say a driver creates multiple accounts, uses the same delivery patterns, and follows the same payout timing. On paper, they look like different users. In reality, it’s the same person gaming the system.
With behavior-level detection, platforms can:
- Detect ban evasion in real time — flag the same delivery flow showing up across “new” accounts
- Link seemingly unrelated accounts — connect multiple identities back to the same pattern of abuse
- Build behavioral fingerprints that persist, even when signals change — so if the driver rotates phones or emails, their tactics give them away
For a ride-share platform, behavior-based signals can uncover entire networks of drivers coordinating to manipulate bonuses. Different names, phones, and vehicles with the same underlying patterns. Once linked, the platform can shut it down.
.png)
The Payoff: Stop Repeat Offenders Without Slowing Down Good Users
Fighting fraud doesn't have to mean adding friction. With behavior-level detection, platforms can finally break the cycle of ban evasion, without compromising growth or experience.
You don’t need to choose between security and scale. You can have both.
Operational wins:
- Block repeat fraud attempts in real time
- Cut down on manual reviews
- Keep your platform clean and your ops team focused
Customer experience wins:
- Preserve a seamless signup for good users
- Protect real customers from fraud spillover
- Build trust and safety at scale
Don’t sacrifice growth to fight fraud. All you need is a smarter way to see who’s really behind the screen. With the right visibility, you can stop bad actors before the damage and keep the experience frictionless for everyone else.
Block Once. Keep Them Out for Good.
Bans don’t stick when you rely on surface signals. Emails change. Devices rotate. Accounts get resold. But behavior is harder to fake.
When you link users by what they do, not just who they claim to be, you can shut down repeat fraud for good. No more chasing fake identities. No more playing catch-up.
Just real-time insight. Persistent protection. And a platform that stays one step ahead.
Want to know how repeat abuse is hiding on your platform? We can show you what to look for. Schedule time with a Spec fraud expert to learn more!
Ready to get started with Spec?
Be'Anka Ashaolu is the Senior Marketing Manager at Spec, the leading customer journey security platform leveraging 14x more data to uncover fraud that others miss. With over a decade of experience driving growth for B2B SaaS companies, she has built a reputation for developing high-impact strategies that fuel demand and elevate brand visibility. Be'Anka earned her degree with honors from Saint Mary’s College of California, majoring in Communications with a minor in English.