The Spec Blog
Your source for fraud-fighting news and insights
Sign up to receive regular fraud industry insights from leading experts in the space.
Categories
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
Product
Nov 17, 2025
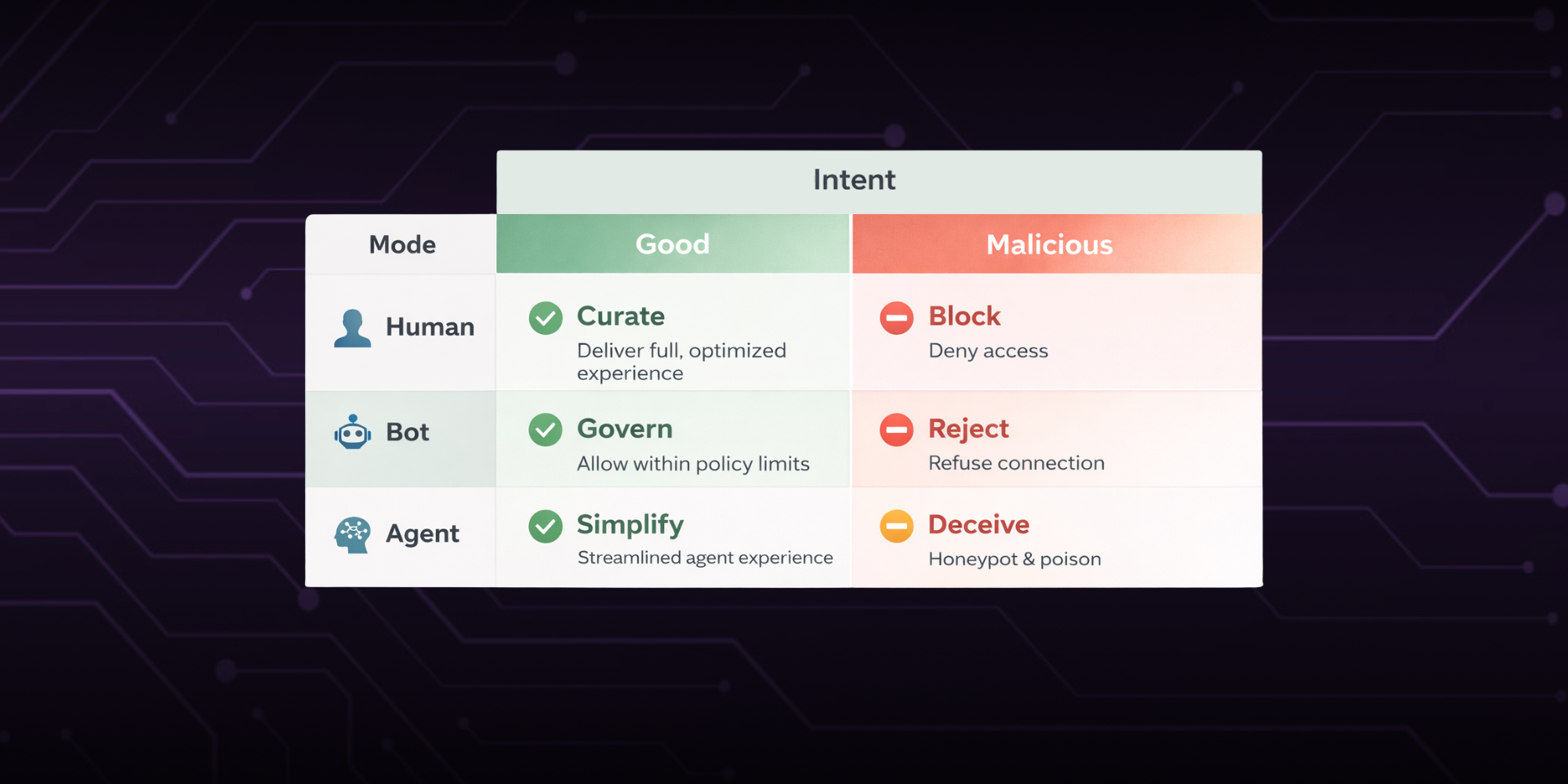
Scaling Product Experiences Without Breaking Trust
For years, fraud prevention sat apart from the customer experience, treated as a safety net rather than part of the design. But that separation no longer holds. In digital products, how you manage trust is how you shape experience.