#35: PayPal & DocuSign phishing scam, startup's card testing attack, 1,800 arrested in global crackdown
This week, we saw a phishing campaign mimicking PayPal and DocuSign, a small eCommerce founder detailing a brutal bot-driven chargeback attack, and a coordinated international takedown of scam compounds exploiting both consumers and forced workers.
Let’s get into it.
NATE'S TAKE - JUNE 10, 2025
Top Three This Week
- Scammers Are Weaponizing Real DocuSign Accounts
- Bot-Driven PayPal Abuse Leaves Startup Scrambling for Help
- 1,800 Arrested in Global Crackdown on Asia-Based Scam Networks
1. Scammers Are Weaponizing Real DocuSign Accounts
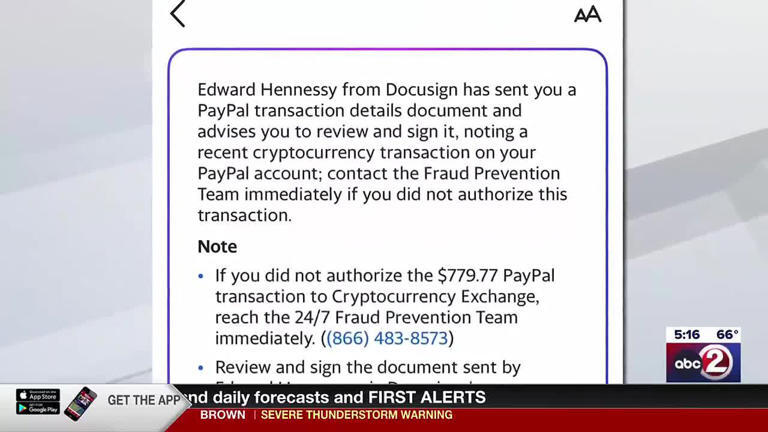
A new phishing campaign is using convincing PayPal-branded emails and real DocuSign links to trick people into signing off on fake cryptocurrency disputes. The catch? Some of the DocuSign accounts are real, created by fraudsters to bypass basic email filtering and appear more trustworthy.
PayPal and DocuSign have both issued public warnings. And according to the FTC, more than 8,000 people in Wisconsin alone reported fraud in Q1 2025, losing over $28 million - with business impostor scams topping the list.
Scammers know users trust these brands.If you're monitoring email-based threats, it's time to widen the scope.
Fraudsters are no longer faking domains. They're abusing legitimate services to sidestep filters. Flag any DocuSign links sent outside of standard business workflows, and build user education around the newest signs of legitimacy misuse.
2. Bot-Driven PayPal Abuse Leaves Startup Scrambling for Help

In more PayPal news, a founder on Hacker News shared how their e-commerce marketplace is being bombarded by small, automated PayPal purchases that are quickly disputed. The attacks appear to use browser automation, rotating IPs, and unverified PayPal accounts to simulate real purchases - a playbook designed to evade basic detection.
Despite using PayPal’s Multiparty APIs, the startup has received little support. PayPal’s team doesn’t see the broader pattern, and insists that each seller file complaints independently. For a small business, that kind of fragmentation is impossible to manage and it leaves attackers free to operate across accounts with no real consequences.
Some tactical advice for founders facing similar issues:
- Track anonymous user sessions: Look for users who skip common pre-payment steps. Even simple session logging can reveal suspicious patterns.
- Add free device fingerprinting: Tools like Thumbmark.js make it harder for attackers to blend in.
- Use free IP reputation services: Services like IPQualityScore (with caching) can help flag known proxies or risky IPs.
- Monitor payment failure rates in real time: If your success rate dips suddenly, trigger stricter controls automatically so there’s no need to wait for a manual response.
No single signal is enough, but combining session, device, and IP intelligence gives you a stronger line of defense. For early-stage companies without a dedicated fraud team, these steps can help buy time and reduce damage until more advanced tools are within reach.
3. 1,800 Arrested in Global Crackdown on Asia-Based Scam Networks

Police in Hong Kong announced that a joint operation across seven countries—including South Korea, Thailand, Singapore, Malaysia, and the Maldives—led to the arrests of over 1,800 people and the freezing of 33,000 accounts.
The scams involved everything from deepfake-enabled business impersonation to online shopping and employment frauds. Authorities successfully intercepted roughly $20 million in fraudulent funds.
One case highlighted a finance director in Singapore who was tricked into transferring nearly $500,000 after a scammer used a deepfake video of his CEO. Through cross-border cooperation, that money was recovered.
The UN says scam compounds in countries like Myanmar, Cambodia, and Laos continue to lure workers under false pretenses, forcing them into virtual slavery to run romance scams, investment cons, and illegal gambling rings.
This isn’t just a local problem - it’s a global criminal economy. Fraud teams should be thinking globally, especially as fraud rings increasingly route funds and exploit victims across borders.
===
That’s all for this week! For more insights, follow us on LinkedIn or X, and if you want to learn more about what we do, visit www.specprotected.com.
Ready to get started with Spec?
Nate Kharrl, CEO and co-founder at Spec, has built leading solutions for application security and fraud challenges since the early days of the cloud era. Drawing from his cyber experience at Akamai, ThreatMetrix, and eBay, Nate helped found Spec to focus on the needs of businesses operating in a landscape of increasing AI risks. Under Nate’s leadership, Spec grew from its mid-pandemic founding to raise $30M in venture-backed funding to build solutions used by Fortune 500 companies transacting billions in online commerce. Spec’s service offerings today include protective measures for websites and APIs that specialize in defending against attacks designed to bypass bot defenses and risk assessment platforms.