#36: Large-Scale ATO Campaign, Bipartisan Fraud Task Force, Behind Fake CAPTCHAs
This week, we’re digging into stories that expose just how creative, coordinated, and large-scale today’s fraud operations have become.
Let’s get into it.
NATE'S TAKE - JUNE 17, 2025
Top Three This Week
- Over 80,000 Microsoft Entra ID Accounts Found Exposed Online
- A Bipartisan Push for a Payments Fraud Task Force
- Behind Fake CAPTCHAs: A Closer Look at the Dark Adtech Fueling Scams
1. Over 80,000 Microsoft Entra ID Accounts Found Exposed Online
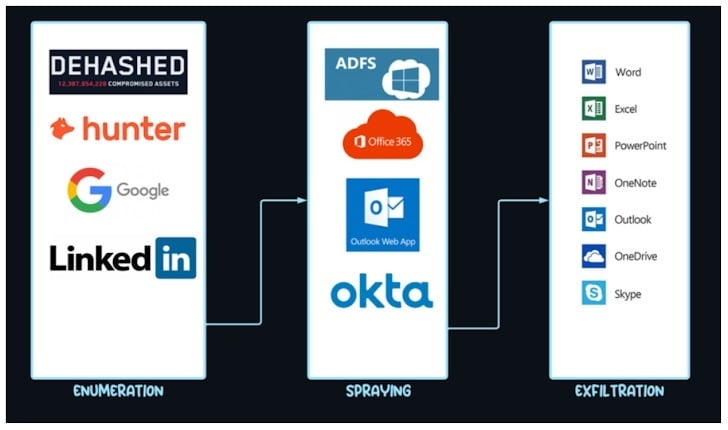
A large-scale account takeover campaign dubbed UNK_SneakyStrike has hit over 80,000 Microsoft Entra ID accounts across hundreds of organizations. Attackers used the open-source tool TeamFiltration to run password-spraying and user enumeration attacks, leveraging AWS servers and the Microsoft Teams API to stay under the radar.
Targeted services included Teams, OneDrive, and Outlook. Smaller cloud tenants were hit broadly, while larger ones saw more selective targeting. At peak, 16,500 accounts were probed in a single day.
This attack shows how legitimate security tools are being turned against enterprises, and how cloud apps are now prime ATO targets. Watch for bursts of login attempts from rotating IPs and don’t ignore quiet periods. They’re often just the calm before the next wave.
2. A Bipartisan Push for a Payments Fraud Task Force

Fraud losses in the U.S. continue to climb: $12.5 billion in 2024 alone, a 25% jump from the year before, according to the FTC. In response, a bipartisan group of U.S. senators introduced the Task Force for Recognizing and Averting Payments Scams Act last week. The bill proposes a formal task force chaired by the Treasury Department, with representatives from the DOJ, CFPB, FCC, FTC, and industry groups.
The mission is to examine the payments landscape, recommend changes to existing laws, propose industry best practices, and improve fraud coordination across local, state, and federal levels. The task force would deliver reports every three years.
Backing the effort are a mix of trade associations and banks including the AARP, American Bankers Association, and Electronic Transactions Association. According to the ETA, fraudsters have long thrived on gaps between regulators, platforms, and enforcers.
While this legislation won’t bring immediate relief, it signals growing momentum in Washington to treat payments fraud as a systemic risk. Coordination across stakeholders is a long-overdue move and one that could finally shift responsibility back onto platforms, tools, and payment rails rather than placing the burden entirely on individual consumers.
3. Behind Fake CAPTCHAs: A Closer Look at the Dark Adtech Fueling Scams
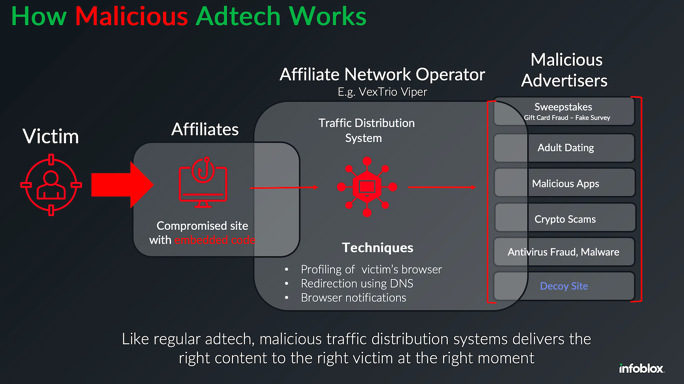
Photo by Infoblox
Brian Krebs recently published new findings on a sprawling malvertising ecosystem that abuses push notifications and fake CAPTCHA popups to target victims on desktop browsers. The key takeaway for fraud fighters? Desktop phishing isn’t just alive, it’s thriving, industrialized, and largely invisible to most defenses.
The bad actors behind these scams use traffic delivery systems (TDS) that redirect users through complex chains of compromised websites and cloaking domains, effectively hiding phishing pages and payloads from both security tools and moderation platforms. These TDSs are what allow malicious actors to buy, sell, and scale scam delivery like any other adtech product.
For fraud fighters, this is a reminder that not all phishing lives in email. The same attention you pay to messaging vectors should apply to web traffic, notification abuse, and traffic cloaking infrastructure. If you're not monitoring how users are arriving at malicious pages - or how attackers are avoiding your controls - you may be missing the full picture.
===
That’s all for this week! For more insights, follow us on LinkedIn or X, and if you want to learn more about what we do, visit www.specprotected.com.
Ready to get started with Spec?
Nate Kharrl, CEO and co-founder at Spec, has built leading solutions for application security and fraud challenges since the early days of the cloud era. Drawing from his cyber experience at Akamai, ThreatMetrix, and eBay, Nate helped found Spec to focus on the needs of businesses operating in a landscape of increasing AI risks. Under Nate’s leadership, Spec grew from its mid-pandemic founding to raise $30M in venture-backed funding to build solutions used by Fortune 500 companies transacting billions in online commerce. Spec’s service offerings today include protective measures for websites and APIs that specialize in defending against attacks designed to bypass bot defenses and risk assessment platforms.