
How Spec Detects AI Agents That Blend in with Real Users
Agentic commerce isn’t a future concern. As of the writing of this blog, some of the enterprise merchants we serve see as much as 25% of their good purchase volumes come from automated sources.
Agentic commerce is here and happening quietly.
These are power users, resellers, brokers, and real-time triangulation agents - acting on behalf of either real users or larger entities. We’ve already seen them shift from brittle traditional bots to AI-driven agents that browse, test, and transact autonomously - the earliest we saw in 2023.
But for every good automated purchase, we see about 20x more automated attacks. These attackers continually iterate to look for weaknesses in detection and mitigation. If their reverse-engineering is successful, they go on to scrape data, test credit cards, create scam content, make fraudulent purchases, abuse business processes, or compromise accounts.
If you’ve seen a disconnect develop between your marketing funnel, your purchasing volume, your customer LTV, and your churn rate, you’re likely in the beginning stages of uncovering how much agentic commerce is already impacting your business today.
AI Agents Look Just Like Customers
Every modern commerce platform already has layers of defense: CDNs, bot managers, CAPTCHAs, device fingerprints, risk checks, and input biometrics. Those tools were built to detect technical signatures, enforce rate limits, and check threat lists.

This was all well and good, but we see this legacy stack crumble easily when pressed by agentic threats. This checkpoint model means agents need only to reverse-engineer two layers of defenses:
- Your bot perimeter
- A single risk checkpoint
After that, their target’s business flows and API endpoints become an extension of the attacker’s agentic infrastructure. They don’t get caught because:
- The agent learns not to trigger rate limits.
- The agent reverse-engineers which technical signatures they need to evade.
- The agent figures out how they need to present identity data in order to get past fraud checks.
Agents will discover whatever it takes to look “good human” enough to achieve their goals. In production, we see these agents complete full flows, view listings, change search filters, revisit pages, and abandon carts because that’s how they’ve learned to look human.
We spot and stop these using a different approach.
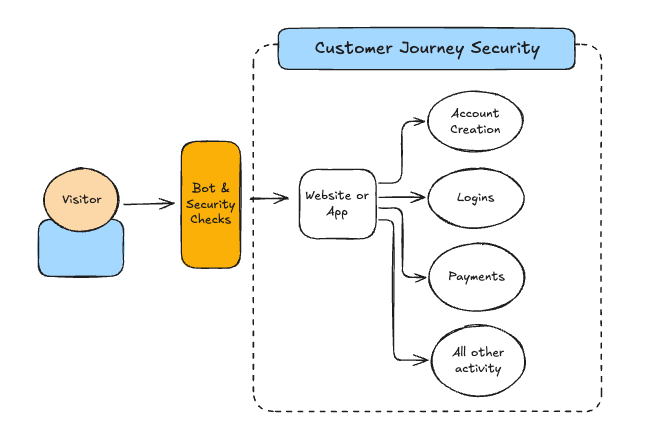
Instead of a narrow risk check embedded deep inside a specific business operation, we monitor, analyze, and categorize the entire customer journey in real time. In practice, this becomes impossible for an agent to fake because the surface area (and memory requirements) of what they need to learn is too large. They effectively have to be good customers in order to look like good customers.
For bad agents, on the other hand:
- Journeys repeat: what noise and variation agents bake in isn’t enough to make them look human.
- They skip optional pages, trigger identical backend calls, navigate impossibly, ask for fake files, and lazily “fuzz” requests.
- “Users” appear to pass MFA and then fail the next step repeatedly.
How Spec Solves Agentic AI Challenges
We get called in when merchants are wrangling with hard-to-tame problems with fraudulent payments, fake signups, card testing, scam content, and refund abuse – all despite having made major investments over many years.
Ultimately, the tools that worked for the last 10+ years now struggle with agent-based attacks because these tools are trapped in silos. Inside these silos, they’re limited to basic velocity, linking, signature, and reputation checks – or worse, blackbox models derived from a mixture of those same siloed checks.
Because agents figure out how to attack the gaps between security, identity, and fraud stacks, it becomes a pesky issue for many organizations to solve because they first need to agree on “who owns this problem in the first place?”
Agent detection and defense feels too technical to be an identity or fraud problem yet too behavioral and identity-centric to be a security problem.
We frequently get asked “is Spec for bots or fraud?” in the attempt to understand which enterprise org should evaluate our product. The answer is “both, and also your customer data platform team.” At Spec, we don’t rely on surface-level signals. We see the entire journey, from the first HTTP request through every interaction that follows. That context is what makes intent visible again.
Here’s how:
1. Full-Journey Visibility
Spec connects at the network layer, through your CDN or edge infrastructure, to evaluate every request and response in real time. We reconstruct each journey end-to-end, stitching clicks, page loads, and API calls into a living map of behavior. This makes it obvious when an “AI shopper” behaves differently from real customers. Bots can spoof devices, but they can’t mimic entropy or human rhythm.
2. Behavioral & Identity Linking
Using Spec ID, we persistently recognize users and devices, even when JavaScript is disabled or cookies are cleared. We tie that identity to behavioral patterns across sessions, devices, and accounts. That’s how we uncover coordinated agent clusters: multiple “users” sharing the same underlying fingerprint, data fragment, or behavioral cadence.
3. Active Adversary Deception
We don’t just detect agents; we trap them. Spec’s honeypots invisibly reroute malicious automation into decoy environments. Attackers think they’re succeeding while we quietly observe, starve them of feedback, and protect your live systems. It’s how one retail client dropped bot-driven payment fraud attempts from 95% to 0.1% over a few months.
4. Real-Time Adaptation
When a new tactic appears – say an AI agent testing refund policies or scraping inventory – Spec adapts in minutes. Because we see the outcomes of every event (login success, payment failure, refund approval), our models self-tune using live journey data without engineering lift.
Proof in Practice
A global retailer recently faced low-and-slow card-testing attacks that evaded rate limits. Spec’s journey analytics caught the pattern instantly. It had the same navigation path, same request rhythm, and different IPs. Within minutes, our models adapted and stopped the campaign cold, without requiring code changes or blocking good traffic.
Another client used Spec’s Honeypot to isolate an AI-driven scraper targeting high-value listings. The attacker spent weeks trapped in a simulated flow, unaware they’d been contained. Real users never saw a slowdown.
These aren’t theoretical results. They’re daily wins from seeing everything the automation touches.
Why Marketplaces & eCommerce Can’t Ignore This
Agentic commerce will increasingly redefine your traffic mix. The increasing pattern is:
- AI shoppers placing orders on behalf of humans.
- Autonomous resale tools flipping inventory instantly.
- Attacker agents adapting defenses faster than your rules can update.
If your system can’t distinguish authorized automation from adversarial automation, you’ll face rising losses, distorted analytics, and declining trust in your data.
The answer won’t be more friction or more CAPTCHAs. Agents know what a bus and a traffic light look like. It’s clarity and the ability to see, interpret, and act on the true intent behind every interaction.
The Spec Difference
Spec combines journey-level visibility, behavioral precision, and identity-aware defense in one platform. Where bot managers stop at the edge, we go deeper. Where fraud tools react to damage, we predict it upstream.
That’s how our customers protect revenue and trust without slowing their product teams or their users.
Ready to See What the Agents Are Doing on Your Platform?
If you’re seeing unexplained traffic patterns, suspicious repeat behavior, or automation slipping through, it’s time to look deeper.
Spec helps fraud and product teams see every click, request, and behavior in context so you can tell whether it’s a customer, a helper, or an adversary.
Talk to our team about mapping agentic traffic on your platform and stopping what your current tools can’t see.
Ready to get started with Spec?
Nate Kharrl, CEO and co-founder at Spec, has built leading solutions for application security and fraud challenges since the early days of the cloud era. Drawing from his cyber experience at Akamai, ThreatMetrix, and eBay, Nate helped found Spec to focus on the needs of businesses operating in a landscape of increasing AI risks. Under Nate’s leadership, Spec grew from its mid-pandemic founding to raise $30M in venture-backed funding to build solutions used by Fortune 500 companies transacting billions in online commerce. Spec’s service offerings today include protective measures for websites and APIs that specialize in defending against attacks designed to bypass bot defenses and risk assessment platforms.




