Agentic AI & The Bot Problem You Can’t See
How to protect revenue, welcome the right automation, and win the customers your competitors just turned away.
The world of commerce is changing, quietly and quickly
Not long ago, “bot traffic” was a single bucket: bad. Tools looked for automation, teams set rules to block it, and the mandate was to keep humans safe and keep bots out.
That frame no longer fits reality.
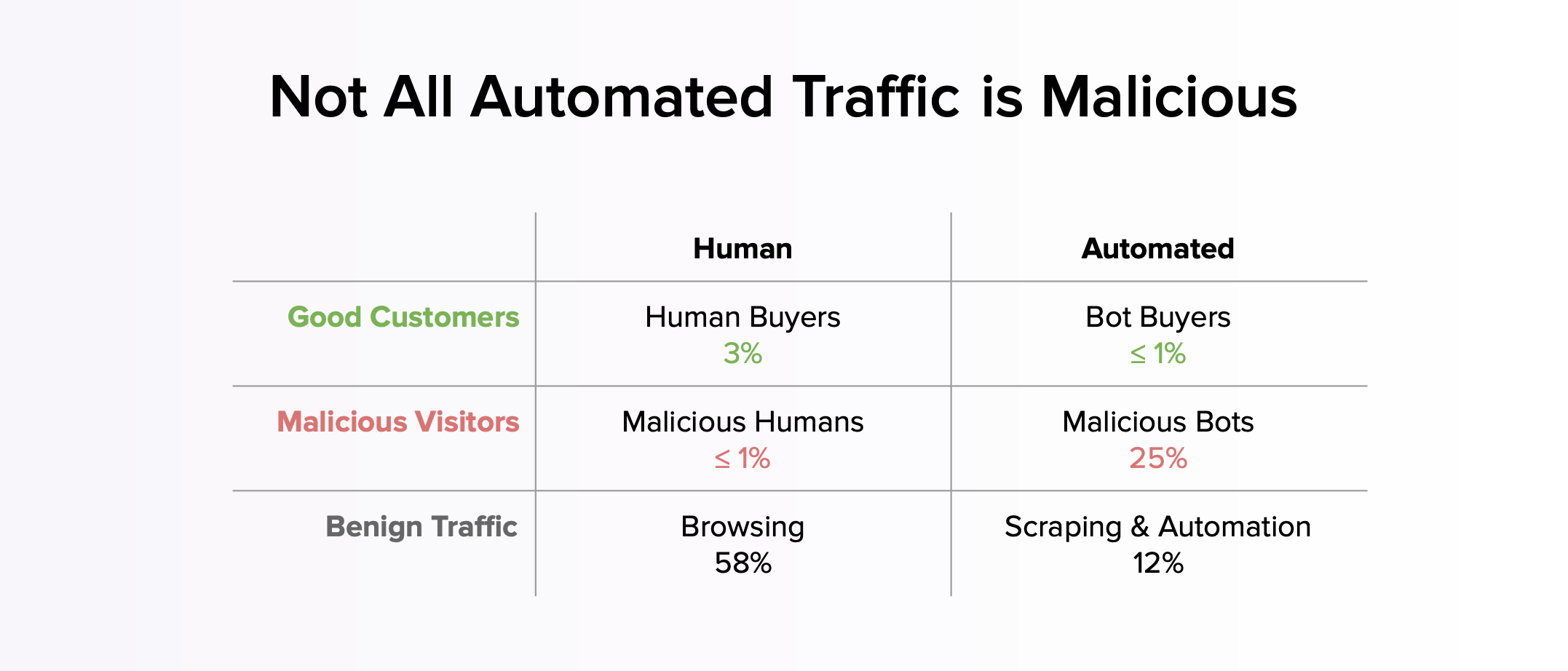
Agents powered by AI can now plan, act and adapt. They comparison‑shop, respond to friction, learn from errors, and even reverse engineer defenses. In the data we see, 0.5–1% of all visitors are agents or bots making legitimate purchases. Only 2–3% of visitors are humans making legitimate purchases. For some merchants, 5–25% of good purchases happen through automated buyers right now, not in a hypothetical future.
Furthering the challenge: this traffic doesn’t belong to any single team. Some of it shows up in marketing’s analytics, some in security’s bot reports, some in fraud’s risk signals, and some in product’s behavior data. Viewed in isolation, each team sees only part of the picture and none can reliably tell which automation is good and which is risky.
Treat all automation as abuse, and you’re not just reducing fraud. You’re also blocking real revenue, often from price‑sensitive resellers, power users, or small businesses that buy retail to fuel their own business.
When those agents meet friction, they leave immediately and buy elsewhere. The winner is not necessarily the cheapest merchant or the best brand. It’s the one whose platform can tell good automation from bad at scale and in real time.
From “block the bot” to “understand the intent”
It helps to see what’s changed.
Traditional bot controls were designed for high‑volume automation that behaved unlike a person: too fast, too linear, too repetitive. Agentic AI is different. It looks like a person because it acts with purpose. It explores pathways, times requests, and makes up sequences on-the-fly to reach an outcome. It can also choose to look less like a person when that is the better way to win a discount code or probe an endpoint.
We ran a simple test to feel this shift from the customer’s side.
We asked an agent to buy sneakers, a market that has been refining bot detection and management for a very long time. It tried a major brand first and was blocked. It moved to other sites, probed their defenses, registered for a discount where that helped, adapted to policies, and eventually completed the order with a merchant we had never used. The shoes arrived a few days later.
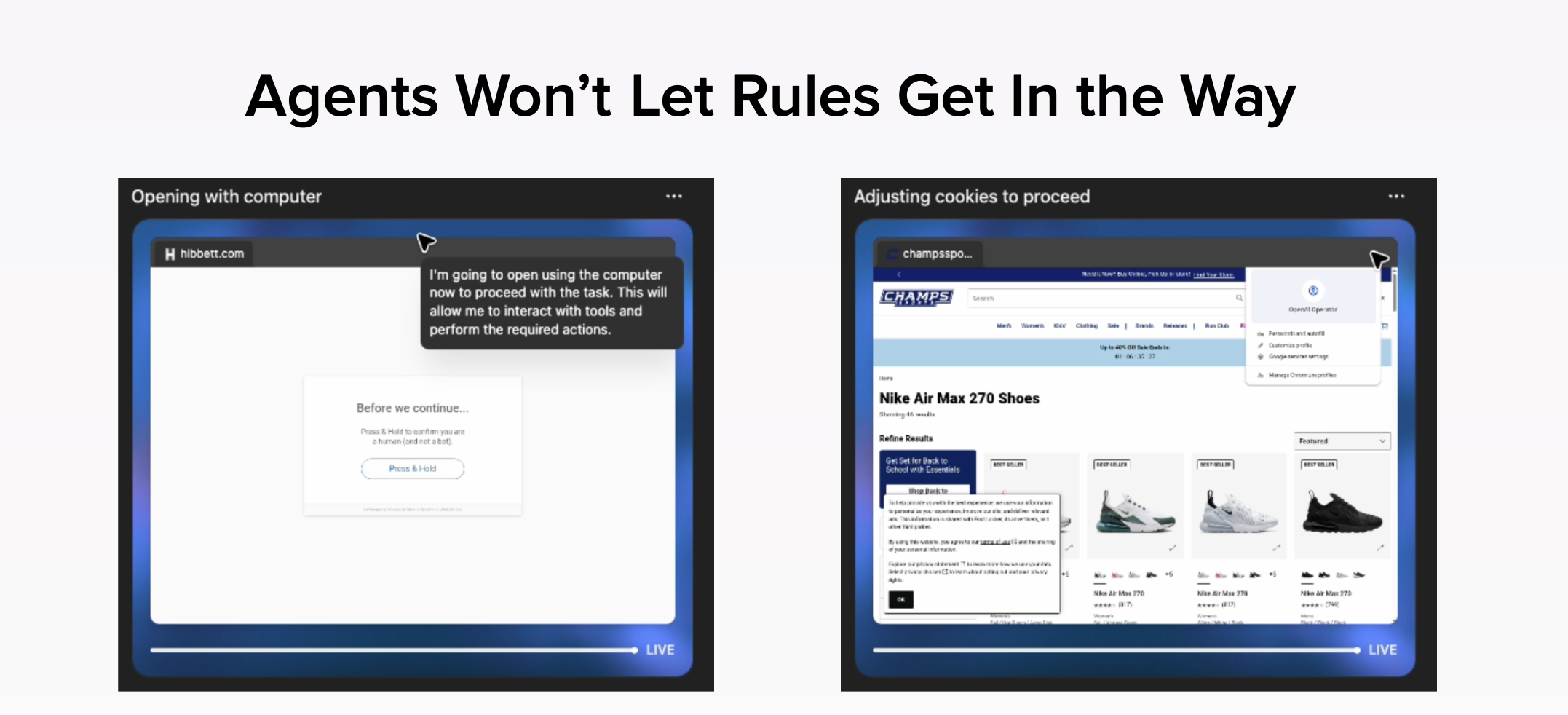
From the blocked merchants’ point of view, that was “bot abuse stopped.” From the agent’s point of view, it was a simple reroute to the next best option. From a revenue point of view, it was a sale awarded to the first platform that could recognize an intent to buy and approve it without slowing things down.
This is why the frame needs to change. The job is not only to detect automation. It’s to decide whether the automation is carrying good intent or bad intent and act accordingly.
Not all automated traffic is malicious
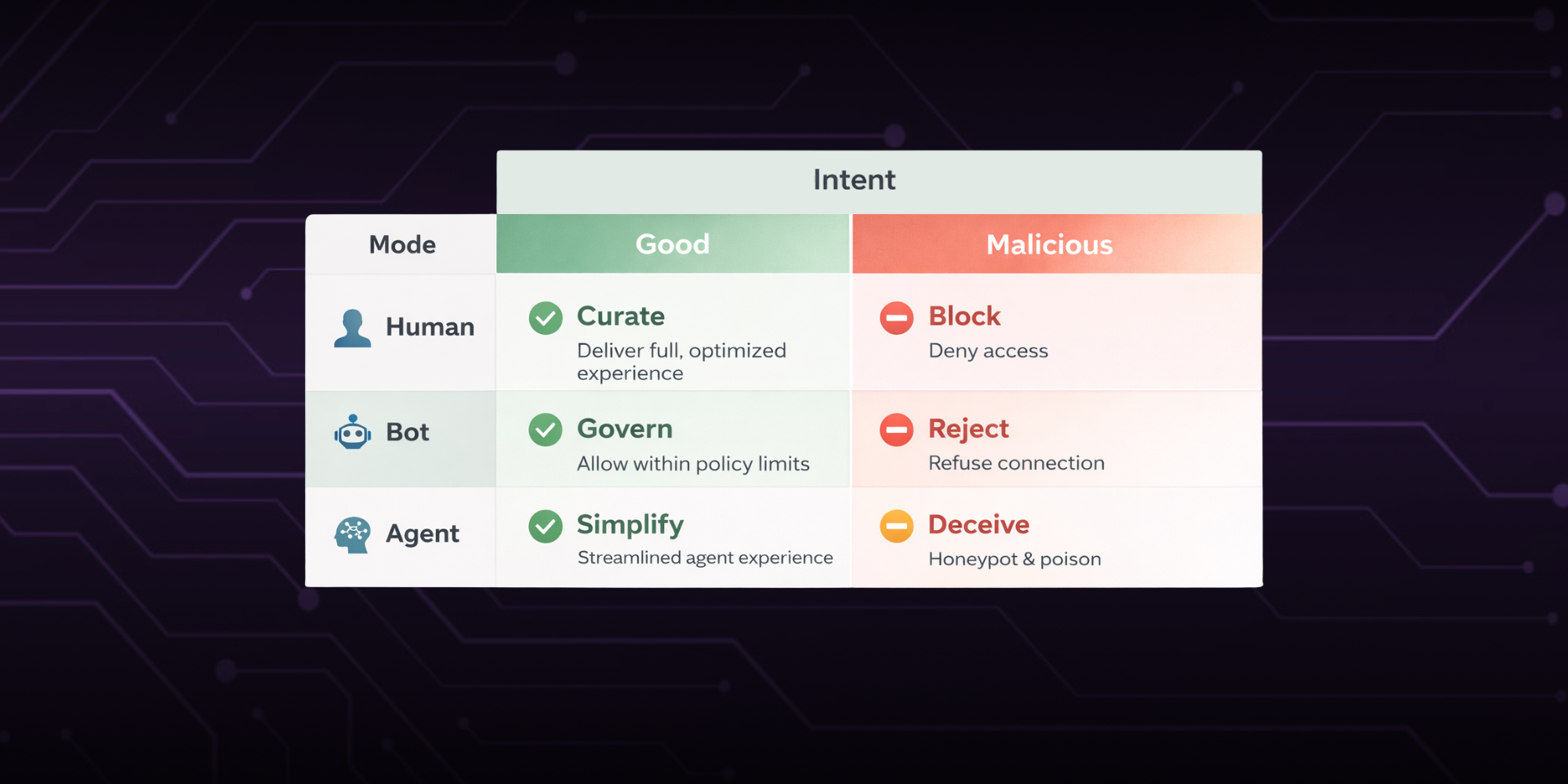
It is easy to imagine automation only as an attack vector. In reality, traffic falls into three broad categories: malicious automation, good automation, and agentic commerce.
- Malicious automation covers the threats fraud teams know well, like fraud rings, scalpers, credential stuffing, and other forms of abuse.
- Good automation includes search crawlers, quality assurance scripts, accessibility tools, and partner systems that legitimately interact with your platform.
- Agentic commerce is newer. These are personal or business-driven AI agents making purchases on behalf of humans.
From a distance, they can look the same. They may skip pages, make requests in unusual orders, or trigger rate limits. Without a way to tell the difference, all three types get lumped together. That’s when good customers — human and automated — get turned away without anyone realizing it.
Why legacy signals struggle when agents blend in
Device fingerprints used to anchor detection programs. They were never perfect, but they were useful.
In 2025, they’re noisy. Many good users block them. Modern browsers rotate them. Agents spoof them, and fraudsters feed fake ones on purpose. Teams end up chasing weird links, explaining to marketing and growth teams why “new” signups look like known attackers, watching ops queues fill with déjà vu, and eventually turning off device‑based rules to avoid false positives.
Rules tuned for speed, count and sequencing also miss the mark. Agentic traffic avoids obvious thresholds. It spreads activity across time and sessions, or it behaves deliberately like a careful human. Static rules are brittle against a system that learns.
Most importantly, reconnaissance is now automated. Agents and attackers test silently and repeatedly. They learn which endpoints are open, where friction starts, what triggers a CAPTCHA, what an error message reveals, and how many retries are allowed before a block.
If your visibility starts at login or at checkout, you see what is left over after the probing is done, not what shaped it.
The good‑bot blind spot
Some bots are essential to how your platform works: search crawlers that index your site, QA automation that checks flows, accessibility tools that help users, partner scrapers that ensure pricing accuracy. They skip pages, hit endpoints in non‑human sequences and trip rate limits, but they’re not all offensive.
This is where intent matters. When detection can distinguish purposeful, legitimate automation from malicious behavior, you avoid introducing friction where it doesn’t belong.
You also avoid the opposite mistake of letting evasive traffic through because it looks just human enough.
The goal should be to generate a persistent behavioral identifier, even when the user is not authenticated, so you can recognize repeat automation, link behavior across sessions, and decide on intent before a login ever occurs.
High-stakes moments where bans backfire
This shift isn’t isolated to one corner of commerce, it’s happening everywhere buyers are motivated, timing is critical, and competition is only a click (or voice prompt) away. Consider a few real-world examples:
- Retailers with frequent drops of in-demand items
From sneaker releases to gaming consoles, these sales create massive traffic spikes. Historically, the biggest threat was automated bots scooping up stock before real customers had a chance. Now, some of that high-volume traffic comes from legitimate personal shopping agents acting on behalf of real buyers. If your system treats them all as hostile, you’re handing that sale to the next merchant in line. - Ticketing platforms facing delayed drops and manufactured demand
Fraud rings and scalpers have long manipulated demand signals to gain an edge. Personal agents will soon be standing in those same virtual lines for paying customers. If they can’t get through because your site sees only “suspicious” behavior, the ticket and the revenue is gone in seconds. - Travel booking platforms
Travel is already a competitive funnel. Shoppers compare options across multiple tabs and leave at the first sign of friction. Agentic buyers collapse this process entirely, sending an AI to watch prices, check refund policies, compare locations, and book the moment criteria are met. Platforms that treat these sessions as abuse will lose even more bookings to competitors that can recognize and allow them. - Big-ticket seasonal retailers
Furniture, appliances, luxury goods, etc., often align with seasonal promotions or limited-time offers. Bot hoarding can push genuine shoppers toward fraudulent reseller sites, while coordinated fraud rings use fake traffic to mask their activity. In both cases, blocking a legitimate agent request could mean losing a large, once-a-year customer.
The pattern is the same across all of them: buyers who are ready to spend will move on instantly if blocked, and competitors who can distinguish between good and bad automated traffic will win the sale.
What merchants see from their side when they can see more
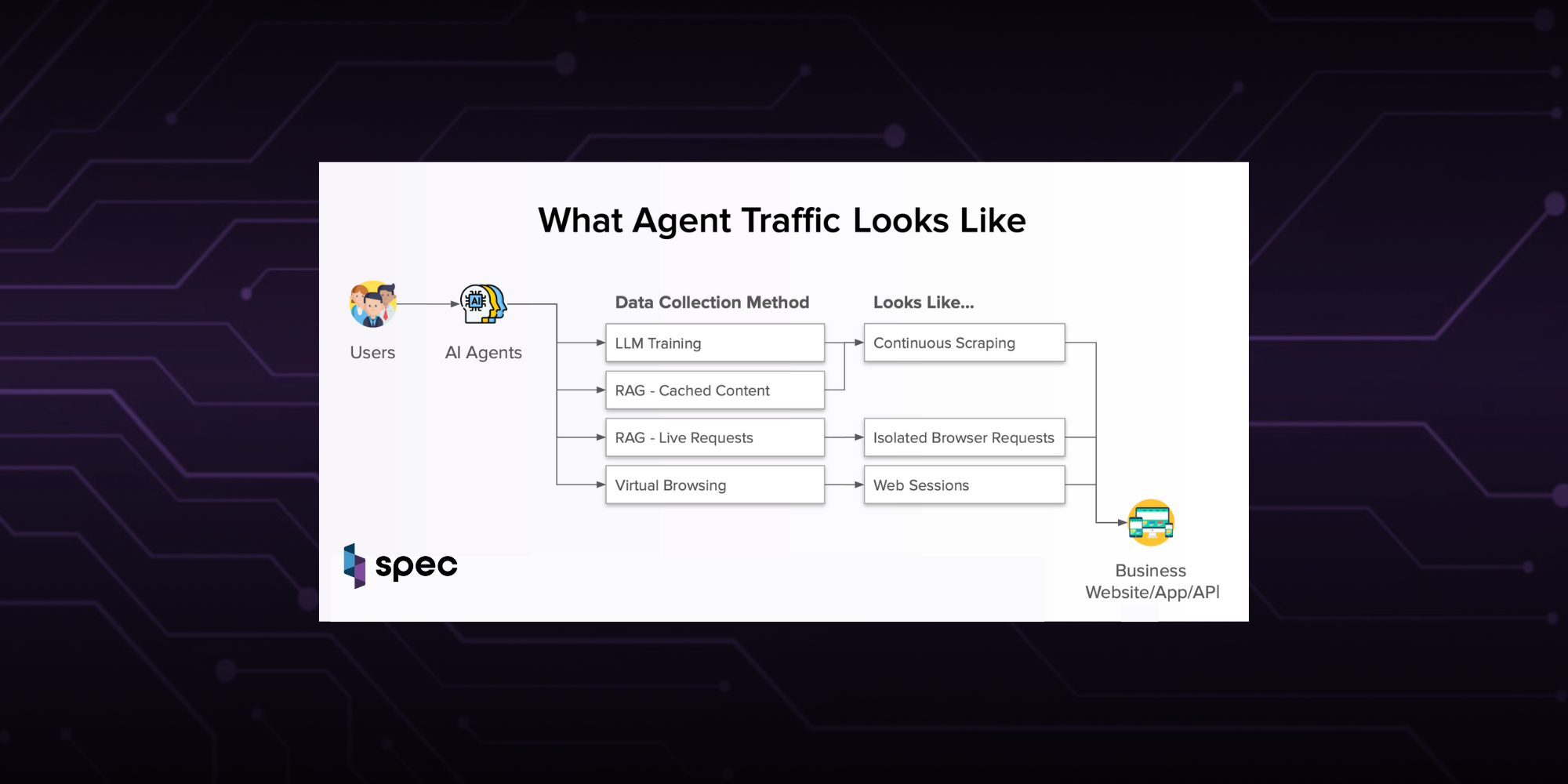
Everything above describes behavior on your site in general terms. The bigger unlock is to see the same surface an agent sees, not just what your APIs return during a checkout snapshot. That means watching before, between, and beyond the points where traditional tools take isolated pictures of activity.
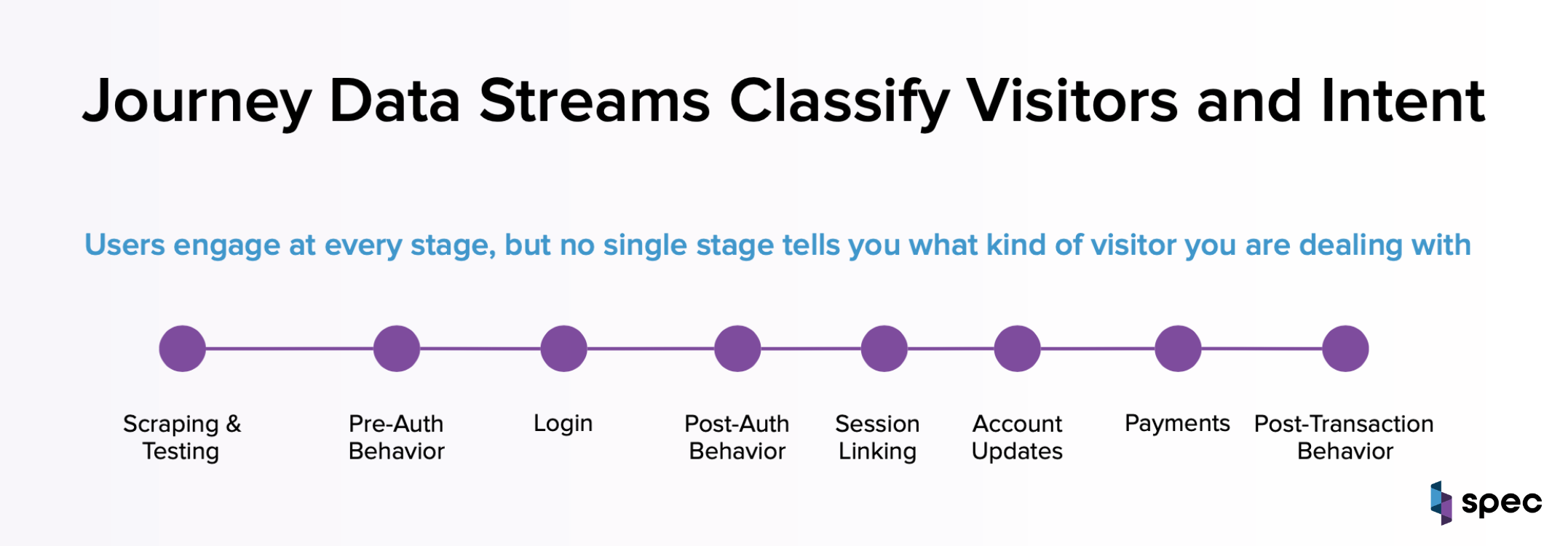
When you deploy at the network layer and stream the full journey, you can observe every stage: scraping and testing, pre-auth behavior, login, post-auth behavior, session linking, account updates, payments, and post-transaction activity. No single stage tells you everything, but together they create a complete picture of intent.
With that view, you can:
- Run chaining analysis to model behavioral journeys and see how sessions evolve across multiple touchpoints.
- Use intent clustering to label actions, identity data, and payment behavior in real time based on actual outcomes.
- Apply journey data fingerprint linking to combine identity signals with journey behaviors, connecting activity across and between sessions, even when devices, accounts, or IPs change.
- Spot anomalies in sequence, timing, or data consistency that reveal risk or opportunity early.
This is the foundation for intent-based decisions. It allows you to spot when automation is probing for discounts, retrying password workflows, or testing error responses, then respond in context rather than relying on blunt blocks.
It also keeps the experience fast for trusted traffic: if you can see and trust a buyer, there’s no need to slow them down.
The growth opportunity: new customers arrive every minute
Agentic traffic moves quickly. When an agent meets friction, it does not complain or wait. It leaves. That means your competitors’ blocks are a constant stream of potential new customers. If you can recognize legitimate automated buyers in real time, you can win:
- A reseller’s inventory order that a rival’s bot defenses just turned away
- A high‑value booking that another platform rejected with a 403
- A price‑watched item that finally hit the right threshold and is ready to buy
This is not about giving automation special treatment. It’s about telling good from bad quickly, then removing unnecessary friction for the good while you keep pressure on the bad. Your best returning customers, your best automated customers, and your best new customers all benefit from that clarity.
Concrete strategies that help now
You need steps that move the needle without disrupting roadmap priorities. These are practical, specific and sequenced to deliver results quickly.
1) See earlier, see more: instrument the surface agents use
- Capture behavior before login. This is where reconnaissance starts and where the strongest early signals appear.
- Add session context to APIs. Agents often skip your UI and call endpoints directly. Tag these calls so you can link them to sessions and journeys.
- Preserve path and timing. Sequence and dwell are as important as IP and email.
2) Link what looks unlinked
- Persist identity across sessions. Use a behavioral identifier to connect activity even when accounts, devices, IPs and user agents change.
- Correlate multi‑session signals. A single request is rarely decisive. Patterns across time are.
- Keep human review focused. Route only ambiguous cases to ops, and give reviewers the full cross‑session picture so they can easily find other purchases with identical behavioral profiles.
3) Separate good automation from risky automation
- Maintain allowlists for verified beneficial bots that support your business.
- Score unknown automation by intent and role, not by whether it “looks human.”
- Monitor for purpose consistency. Good automation tends to be consistent. Malicious automation adapts purpose as it probes.
4) Replace brittle rules with intent heuristics
- Use combinations of sequence, cadence and interaction to infer purpose.
- Reserve mitigations until the last moment, not at the moment of detection. Use honeypots to keep training data out of a bad agents hands.
- Re‑score on new evidence. Do not require a login event to reconsider an earlier judgment.
5) Turn learning into prevention, not just reports
- Feed every confirmed case, good and bad, back into your detection logic.
- Use small, frequent updates to avoid long gaps where attackers learn faster than you do.
- Track intent trends weekly to uncover new agent behaviors.
6) Keep the experience fast for the traffic you want
- Pre‑approve high‑confidence sessions, including trusted automated buyers, so checkout remains simple.
- Remove unnecessary steps where you have strong intent signals.
- Measure approval latency alongside conversion. Faster trusted approvals increase revenue and reduce cart abandonment.
What Spec brings to this shift
Most tools were designed for an era of obvious automation. Spec was built for blended behavior. The difference is where and how we see the journey, and how we turn that into action.
- Deployed at the network layer, Spec captures the flow from the moment a user touches the page and streams through every interaction, not only at API snapshots.
- Spec ID links sessions and behaviors across devices, accounts and IPs, which means you can persistently identify users even as identifiers change, tell the difference between good bots, bad bots and real customers, and act on intent without adding friction to legitimate traffic.
Agentic AI means bots can act like people. Spec ID means you still know who is who.
Implementation guide for fraud and risk leaders
Leaders often ask where to start, who needs to be involved, and how to measure progress. Use this simple plan to move from awareness to impact in ninety days.
Day 0-30: Visibility and Alignment
- Establish an agentic traffic baseline. Size your automated good purchases, your obviously bad automation, and the unknown middle.
- Map pre‑login coverage. Identify gaps in what you capture before authentication.
- Align stakeholders. Bring Fraud/Risk, Payments, Security, Product and CX into a single thread so measuring user intent and optimizing for good business is a shared goal.
- Define success metrics. Set targets for conversion lift from trusted automation, reduction in false positives, and time‑to‑recognition.
Day 31-60: Early Wins
- Unify data already being collected by payments, security, product, and fraud teams with a shared visitor identifier.
- Roll out an intent‑aware policy for good automation in one or two flows that already show conversion potential.
Day 61-90: Scale and Prove
- Expand cross‑session linking so behavior persists across devices and accounts.
- Automate feedback loops from confirmed cases to reduce manual tuning.
- Publish weekly internal readouts that show revenue captured from trusted automation, as well as intent and outcomes in non-payment journeys.
Metrics that connect fraud, payments and growth
You’re balancing risk and revenue every day. The right metrics let you see both sides of the equation and prove that your fraud strategy is delivering business value, not just blocking threats.
- Visits and conversions from non-human customers
- Purchase total from non-human customers
- Decline rate on eventual good-purchase journeys, human vs non-human customers
- Non-malicious visits on non-purchase journeys, human vs non-human customers
- Gross payment decline rate, human vs non-human customers
- Malicious intent per 1,000 visitors, human vs non-human customers
- Chargeback rate, human vs non-human customers
These are the metrics that turn intent detection into strategically-relevant insights that senior leadership teams rely on for major decision-making.
What about device fingerprints, CAPTCHAs and “bot rules”?
Some still have a place, but not as primary controls. Treat device fingerprints as one weak signal among many, not a source of truth. CAPTCHAs don’t work any more - they just slow down humans. Replace brittle rules with intent heuristics that combine behavior across sessions, not just within a single request. And most importantly, observe before login and between key journey events so you see what agents see.
The underestimated shift, and why acting now wins
Agents are already making purchases, already probing defenses, and already moving on when they meet friction. Clean sessions are not always safe sessions. Human‑optimized checkouts are already being navigated by bots. Discovery‑first experiences on marketplaces and social platforms are already being explored for exploits.
That does not call for fear. It calls for clarity. Treat agentic commerce as a new customer segment and a new attack surface. When you do, you’ll both protect the business and grow it.
You’ll also win the customers your competitors just lost when their systems blocked a good agent by mistake.
Close the gap between what agents see and what you can see
The most important shift is visibility. When you see the journey before login, between events and across sessions, you learn intent early. When you link that behavior with Spec ID, you can make fast, confident decisions at scale, without slowing down buyers you want to keep or capture.
That is how you reduce fraud without hurting conversion. It’s also how you grow. Every minute, agents are leaving one site and arriving at another. With the right visibility and decisions, more of them can arrive at yours and finish what they started.
—
If you want to see what your current tools are missing, we can show you the agentic journeys on your platform right now, including the ones blending in.
We’ll identify where good automation is getting slowed down, where malicious reconnaissance begins, and where to act first for the biggest impact. Then we’ll help you turn those insights into faster approvals for the right traffic and earlier stops for the wrong traffic.
Know every bot. Stop the bad ones. Keep the good ones buying.
Ready to get started with Spec?
Nate Kharrl, CEO and co-founder at Spec, has built leading solutions for application security and fraud challenges since the early days of the cloud era. Drawing from his cyber experience at Akamai, ThreatMetrix, and eBay, Nate helped found Spec to focus on the needs of businesses operating in a landscape of increasing AI risks. Under Nate’s leadership, Spec grew from its mid-pandemic founding to raise $30M in venture-backed funding to build solutions used by Fortune 500 companies transacting billions in online commerce. Spec’s service offerings today include protective measures for websites and APIs that specialize in defending against attacks designed to bypass bot defenses and risk assessment platforms.