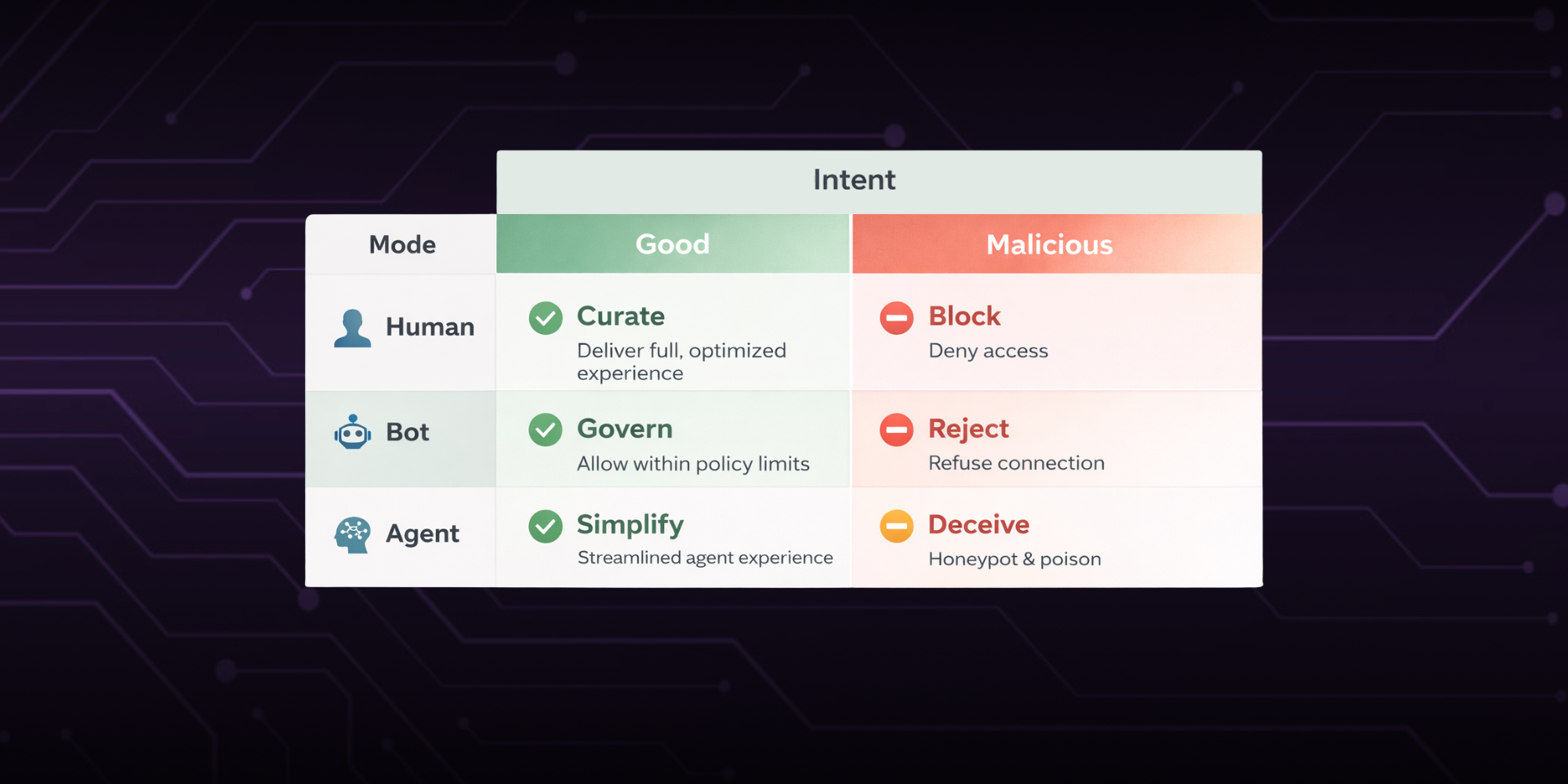
How to Detect and Disrupt Attacks Without Tipping Off the Attacker
Blocking suspicious behavior as soon as it’s detected works in theory. But in practice, it creates blind spots, adds friction, and gives attackers useful feedback.
When you block someone mid-session, you confirm that you saw them. And when fraudsters know they’ve been detected, they adjust. They rotate IPs, change devices, and return under a different identity. Blocking becomes part of their learning process.
Spec takes a different approach. Instead of kicking attackers out, we quietly move them into a honeypot: a fully functional version of your application that looks and behaves like the real thing, but exists solely to observe and contain fraud.
Honeypots are not a new concept in cybersecurity, but they are almost entirely absent from fraud prevention. Most teams aren’t doing this at all. Those who’ve tried have deployed decoy forms or basic traps that are easy for attackers to identify. Spec is the first to make honeypotting usable, invisible, and effective in real customer environments.
The Problem: Blocking Ends the Conversation Too Early
When fraud tools block a session, they also stop collecting useful data. Teams lose visibility into:
- What data the attacker was using
- What their tools and tactics look like
- What they were trying to do next
This also creates operational issues:
- Teams are forced to act on incomplete signals
- Legitimate users are sometimes blocked or forced through added verification
- Models improve slowly because they lack high-quality examples of real attacker behavior
The result is a reactive posture. Teams are constantly responding to alerts, trying to trace activity back to its origin, and manually tuning risk logic after the fact.
The Solution: Observe First, Act with Confidence
Spec’s honeypots solve this by shifting the order of operations. Instead of blocking suspicious users immediately, we route high-risk sessions into isolated environments where attackers can continue interacting—but without causing harm.
What makes Spec’s approach different:
Indistinguishable from production:
The honeypot uses the same interface, logic, and API behavior as your real customer experience. It doesn’t look like a decoy, because it isn’t one. It’s a sandboxed version of your own app, deployed invisibly when risk thresholds are met.
Triggered dynamically based on live risk signals:
Honeypots aren’t active by default. They’re injected only when specific behavioral patterns, device signals, or session anomalies indicate elevated risk.
Integrated with session-level intelligence:
As the attacker moves through the honeypot, Spec collects rich data on their behavior: navigation flow, payload structure, retries, timing patterns, and more. These signals are immediately available for investigation, modeling, and automated response.
The Results: What Customers Are Seeing
Spec honeypots are already delivering measurable impact across high-value flows like login, signup, and checkout.
RELATED: Honeypotting White Paper
Case Study: Stopping Account Takeover at Scale
Challenge:
A global consumer platform was under heavy credential stuffing attacks—millions of login attempts per day. Blocking was causing friction for real users and overloading backend infrastructure.
What they did:
Spec deployed dynamic honeypots on the login flow. Suspicious sessions were silently routed into an isolated version of the experience that mimicked the real authentication flow.
Outcomes:
- 90% reduction in account takeover pressure
- Less than 1% of signups came from malicious traffic
- Millions of credential stuffing attempts were absorbed without triggering alerts or overloading backend systems
- Backend systems were preserved for legitimate users
Case Study: Disrupting Payment Fraud Probes
Challenge:
A digital merchant was targeted by fraudsters testing stolen card numbers. The attacks were subtle and low-volume, but still caused downstream risk and liability.
What they did:
Spec introduced honeypots in the checkout flow. The fake flow returned realistic responses that mimicked processor latency and error conditions.
Outcomes:
- 87% drop in payment fraud attempts
- 25% increase in authorization rates after fake transactions were removed from the flow
- False positive rate remained below 0.1%, preserving the experience for good users
In both cases, honeypots did more than reduce risk. They gave teams the data to understand what attackers were trying to do, how they were doing it, and how to prevent it going forward.
Why This Matters
Spec’s honeypots help fraud teams move from reacting to alerts to proactively understanding attacks.
When you have full visibility into attacker behavior, you can:
- Train better models with real-world behavior, not synthetic data
- Reduce false positives by acting on complete context
- Respond with precision, not guesswork
Instead of blocking and losing visibility, honeypots let you observe first and act with confidence.
Conclusion
Honeypotting is not yet a standard tool in the fraud prevention playbook, but it should be. It solves a real problem: the loss of context and intelligence caused by premature blocking.
Spec makes it possible to deploy honeypots at scale, without disrupting your customer experience or relying on brittle decoy environments. The outcome is stronger detection, better signal quality, and a more confident response to emerging threats.
Fraud doesn’t stop at detection. The teams who succeed are the ones who take time to understand what’s happening before deciding how to respond.
Spec gives them that time and the visibility to make it count.
Download our Honeypotting white paper to learn more.
--
Get Started with Spec
Getting started with Spec is simple and fast. We designed integration to eliminate common barriers and accelerate time to value:

- No major re-instrumentation required: Sessions automatically start when users land on your site or app.
- Lightweight integration: API calls are linked to sessions in real-time through simple configuration.
- Spec ID activates immediately: Returning users are fingerprinted and connected across sessions as soon as integration is live.
- Full support and onboarding: Our team guides your integration process, ensuring fast time-to-value.
You don’t need to rebuild your fraud stack to start seeing full customer journey visibility. Learn more.
Ready to get started with Spec?
Patrick Chen is the Co-Founder and COO of Spec, where he helps businesses fight fraud without sacrificing customer experience. With a career rooted in building technology platforms to solve complex business problems, Patrick has spent years at the intersection of fraud prevention, compliance, and customer journey optimization. At Spec, he's focused on giving teams the ability to adapt quickly to evolving fraud patterns, reduce operational and engineering costs, and eliminate friction for good users.